Boeing and IFE experts are hitting back at claims in a FBI report that suggest security researcher Chris Roberts hacked an inflight entertainment system, gained access to engine controls and issued a climb command resulting in a “lateral or sideways movement of the plane”.
On 15 April, Roberts landed in hot water when he published the following tweet on board United:
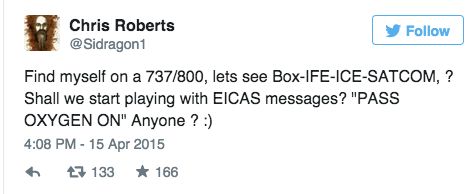 The fallout from this tweet was swift. The FBI detained Roberts at the airport, and confiscated his digital devices. And United later barred him from flying to San Francisco, where he was scheduled to present at a security conference. He flew Southwest instead.
The fallout from this tweet was swift. The FBI detained Roberts at the airport, and confiscated his digital devices. And United later barred him from flying to San Francisco, where he was scheduled to present at a security conference. He flew Southwest instead.
But Roberts was already on the FBI’s radar, having interviewed with a special agent in February and March about what he had identified as vulnerabilities with IFE systems on Boeing 737-800, 737-900, 757-200 and Airbus A320 aircraft.
In its warrant application the FBI says Roberts admitted to compromising Thales and Panasonic seat-back IFE systems “approximately 15 to 20 times”, during the period of 2011 to 2014, and that he claimed to have hacked the systems by gaining physical access through the Seat Electronic Box under the seat in front of him “by wiggling and squeezing the box”. After removing the cover of the SEB, he would use a Cat6 Ethernet cable with a modified connector to connect his laptop to the system, and from there connect to other systems on the network, says the FBI report.
According to the report, Roberts said he “overwrote code on the airplane’s Thrust Management Computer” while aboard a flight, and “successfully commanded the system he had accessed to issue the ‘CLB” or climb command. He stated that he thereby caused one of the airplane engines to climb resulting in a lateral or sideways movement of the plane during one of these flights.”
Airframers and IFE stakeholders are loathe to say definitively that their systems cannot be hacked because doing so may have the undesired effect of further challenging black hat hackers.
But when reading the FBI search warrant application for Roberts, it’s important to consider that IFE systems on commercial airplanes “are isolated from flight and navigation systems”, Boeing said in a statement after myriad news titles reported the FBI claims as fact.
“While these systems receive position data and have communication links, the design isolates them from the other systems on airplanes performing critical and essential functions.”
IFE is typically certified to Design Assurance Level (DAL) E under the FAA’s DO-178B software guidance for airborne systems. Level E is the least stringent level of rigor put into design, verification and testing, as a fault is expected to have no effect on the safe operation of the aircraft. By contrast, radios are certified as Level D and avionics are Level C.
There are ARINC 429 connections to IFE systems (for mission data) “that are not segmented as diligently as with ARINC 664 Ethernet domains. It would take software manipulations to control the 429 interfaces from a compromised Ethernet connection. Regardless, the IFE ARINC 429 interfaces are not capable of changing automatic flight control modes,” notes industry expert Peter Lemme, who chairs the AEEC subcommittee that builds standards for Ku and Ka satcom systems.
“The claim that the Thrust Management System mode was changed without a command from the pilot through the mode control panel, or while coupled to the Flight Management System is inconceivable,” he adds.
In a post 9/11 world, the further claim that Roberts tried to hack IFE systems multiple times by direct physical interface also seems fantastical, says IFE industry consultant Michael Planey. “We have seen multiple instances of passengers being restrained by fellow passengers or flights diverted because a passenger is behaving abnormally. I find it nearly impossible to believe Roberts could have done this type of an act over a dozen times and never had a flight crew or fellow passenger notice – that part stretches the imagination. Furthermore, in the event that what he claims about monkeying with the Thrust Management System occurred, that would have been noted by the flight crew; they would have noticed the aircraft was moving not by command from the cockpit. There would have been many ways in engine monitoring and flight control management systems to detect this sort of event, and I would have expected the pilots would have written it up and there would have been an investigation. So I don’t believe what he says to be true.”
Lemme adds, “Thrust Management has always relied on the pilot as an active monitor for failure, and the pilot has complete authority to override any failure mode.”
Boeing says that while it is “committed to designing airplanes that are both safe and secure – meeting or exceeding all applicable regulatory requirements for both physical and cyber security” – it does not discuss specific airplane design features for security reasons.
Panasonic says, “We take the security of our inflight entertainment and communications systems very seriously. We have stringent and evolving requirements to ensure the highest standards of safety but, for obvious reasons of security, we don’t disclose the details of those systems’ security measures.”
However, if it’s discovered that Roberts made a hacking attempt as described in the FBI report, he “should face the full force of the criminal justice system”, suggests Planey, “because as has been said better by others, intent is irrelevant when it comes to unethical hacking. If you’re intentionally trying to compromise flight operations, you’re guilty of a crime and you’re endangering the lives of a lot of people and that’s a long way to go to just prove a point.”
For his part, Roberts identifies as a white hat hacker. He has reportedly suggested that context is missing from the FBI report, and his most recent tweets indicate he is not saying more at this time.
Setting the Roberts saga aside, there are some real security vulnerabilities in aircraft. But, by and large, catastrophes represent a sequence of events, any one of which could have prevented the outcome. There might be one main contributor, but there are still other attributes.